Displaying items by tag: Symantec
CA/Browser Forum Changes Will Break Many Existing Networks
 |
We have a new winner of the “what were they thinking award” the CA/Browser Forum have won this one by changing the way that certificates are issued. Normally such changes are not intrusive and are intended to ensure better security for users. However, in this case the changes published in July of this year (and set to take effect in November 2015) will probably break a significant number of corporate networks simply because the changes are in direct opposition to the best practices that Microsoft and many others have been recommending for years. This is the practice of separating internal and external domain names for security and identification. The CA/Browser Forum announced back in July that they are going to put an end to this practice by November 2015.
Windows 8 and RT Security; The Good the Bad and What It All Means
 |
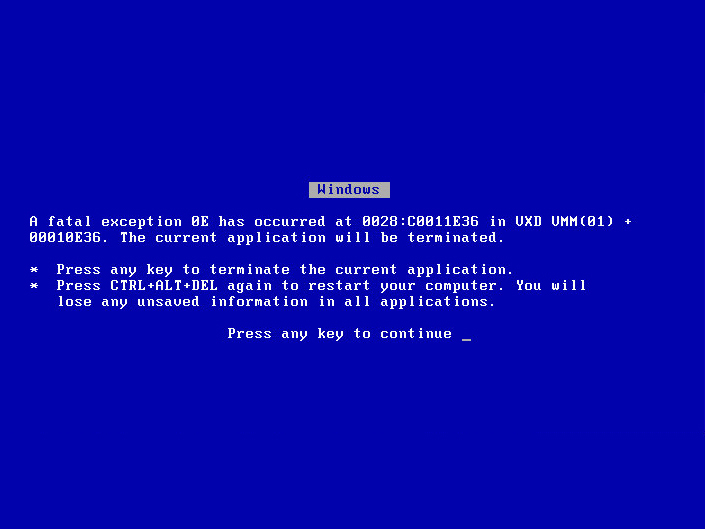
As we have been working with Windows 8 and Windows 2012 server we have become increasingly concerned about security. Although Microsoft has claimed that they have improved security through items like the locked UEFI boot process there are still glaring omissions in security that keep popping up very recently it was noted that despite the claims from Microsoft of a more secure login process the password hint is exposed in the SID database and easily recovered remotely. We also found that users’ contact lists are also left in the open (and in plain text) and available to anyone that can gain remote elevated privileges; which is what almost all Viruses and Malware try to do.
New Shamoon Malware May Be An Effort to Copy Flame
 |
Another day another bit of malware hits the internet. This time the malware is a very nasty bit of code and one that you should be very concerned about. The new malware named Shamoon was first reported on Thursday and has the nasty capability to grab user information before attempting to render the system unusable. Both Symantec and Kaspersky have independently reported on the malware and from their reports on the new bug seem to feel it is definitely worth keeping an eye on.
New Malware Threats Increase For Smart Phones As They Become Primary Devices For Browsing, Banking And Entertainment
 |
There is trouble in the Google Play Store as someone (Symantec) has discovered a Trojan downloader application that appears to be rather prevalent in the form applications masquerading as different applications (two of the most downloaded were Mario Brothers and GTA 3 Moscow City). The new malware appears to be concentrating on the Eastern European area right now as it utilizes premium SMS services that are tied to specific regions using certain numbers.
Symantec Joins the NSA in Spreading FUD...
 Symantec, perhaps in an effort to reclaim some of their reputation, has released a report claiming that some people involved in the DDoS attacks after the MegaUpload take down may have been tricked into downloading a data stealing virus. In a post on Symantec’s own blog they have built a nice (and plausible) timeline of events complete with images (although no links) showing how this happened right around the 20th of January. Many news sites have picked this up and are busy wirting articles about how Anonymous has been hacked... Now the question is, is any of this true?
Symantec, perhaps in an effort to reclaim some of their reputation, has released a report claiming that some people involved in the DDoS attacks after the MegaUpload take down may have been tricked into downloading a data stealing virus. In a post on Symantec’s own blog they have built a nice (and plausible) timeline of events complete with images (although no links) showing how this happened right around the 20th of January. Many news sites have picked this up and are busy wirting articles about how Anonymous has been hacked... Now the question is, is any of this true?
Anonymous releases PCanywhere source code to the wild
 There are just some things that you should not do. One of those is never start a land war in Asia… um sorry wrong article; well one of the others you should never think that dealing with Anonymous is all fun and games, or that the collective can be bought or treated with the same type of disregard as a common criminal. We have been following the spat between Anonymous and Symantec for some time and the feud actually goes back farther than many people think.
There are just some things that you should not do. One of those is never start a land war in Asia… um sorry wrong article; well one of the others you should never think that dealing with Anonymous is all fun and games, or that the collective can be bought or treated with the same type of disregard as a common criminal. We have been following the spat between Anonymous and Symantec for some time and the feud actually goes back farther than many people think.
New Malware Found with Stuxnet Similarities
 Just in case all of the warnings that we gave you before about SCDA (Supervisory Control and Data Acquisition) devices and how insecure most of them are was not enough. We now find that a new piece of malware that appears to be intended spy on industrial networks as a precursor to a future attack like the Stuxnet malware that hit last year. Dubbed Duqu because of a prefix attached to files the new malware creates this new bit of code is very concerning to security experts.
Just in case all of the warnings that we gave you before about SCDA (Supervisory Control and Data Acquisition) devices and how insecure most of them are was not enough. We now find that a new piece of malware that appears to be intended spy on industrial networks as a precursor to a future attack like the Stuxnet malware that hit last year. Dubbed Duqu because of a prefix attached to files the new malware creates this new bit of code is very concerning to security experts.
The code was found on several Windows based systems across multiple companies in Europe. These companies were not directly identified but all appear to have connections to industries that directly interact with basic infrastructure services. As of right now Duqu appears content to just gather information and report back to its command and control servers (including using an internal key logger). Duqu also appears to be sending JPG files back and forth between the server and the infected system, but as many found out to their dismay you can embed quite a bit of information in a JPG files so these could be used to send control instructions and responses or could be nothing more than test files right now.
So far researchers are at a loss as to what Duqu is collecting and why this is happening. They do know that the attacks have been going on since at least December 2010 and that the first variant identified used a stolen certificate much like the original Stuxnet did. Researchers at Symantec and McAfee also feel that the creators of this code had access to the source code of Stuxnet as the two pieces of Malware are very similar in the way they operate and the coding used. Both McAfee and Symantec have also stated that Duqu does not spread and that it does not appear to use any known exploits. This would indicate that the malware uses tactics like drive-by, or social engineering based exploits. These rely on human intervention to download and install the malicious code on a system usually via email or web link.
We personally wonder if this is related to some of the rumors about Anonymous stepping up their attacks on Governments and Large Corporations. After all with what they can gather using some fairly simple techniques (and a nice bit of coding) they can put some rather devastating plans into action very quickly. If this is the case (and this is all just speculation) then we might be looking at an attack that no one is really prepared for. Then again this could all be nothing more than a reconnaissance mission, especially considering the fact that the code uninstalls itself after 30 days…
Source Symantec and McAfee
Discuss this in our Forum
