The Ultimate Kronos Group was the target of a Ransomware attack in Late 2021 coincidentally at the same time the Log4Shell vulnerability was disclosed. Kronos has not disclosed how the ransomware got into their environment, nor has it been revealed who might be behind the attack. Original estimates were that Kronos would be able to restore the impacted systems and be back online in a few weeks. Now, a bit more than a month later, there have been no real updates on the situation and many organizations are still feeling the effects.
- Details
- By Sean Kalinich
- Hits: 2959
Read more: More Than a Month After Being Hit by Ransomware...
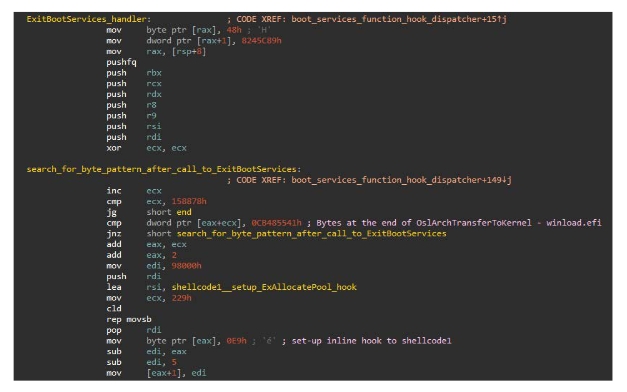
APT group 41 also known as Winnti has been tied to a wonderful new piece of malware that does not infect your operating system, but the UEFI firmware on your device. The malware in question has been dubbed MoonBounce by the security researchers at Kaspersky who are responsible for finding it. APT41 has been in operation for a while and is identified by their tactics techniques and protocols (TTPs) which include stealthy attacks meant to maintain a long-term presence for information gathering on the target.
- Details
- By Sean Kalinich
- Hits: 1184
SaaS is the de facto way of doing business for the SMB (and even for the enterprise). The costs of building your own infrastructure and maintaining it are just too high for most. Instead, it is easier and more cost effective to let someone else handle it. Buying a spot in Amazon Webs Service, Google Cloud Platform, or Microsoft Azure it not complicated and the tools to help you set up your new business infrastructure are well done (if not always well documented). When you use these services, you do expect them to provide security, but what you may find out is that not all cloud vendors think that should come as part of the package. In fact, many look at them as little more than a way to gain extra revenue and not something that just should be done.
- Details
- By Sean Kalinich
- Hits: 1107
The current threat landscape has user account compromise and endpoint takeover as the most common first acts in a security event. The methods used to accomplish this are varied but include such blockbusters as poisoned websites and URLs embedded in email. Once the website is processed the exploit kicks off and things tend to go downhill from there. The most common item abused in your web browser is its ability to process scripts (especially JavaScript). Now Microsoft says they have a way to knock out as much as 45% of exploit attempts related to JavaScript and WebAssembly when using their Chromium based Edge browser.
- Details
- By Sean Kalinich
- Hits: 1414
Remember the days when browsing the internet was simple, all you had to worry about was clearing your cookies and browser history and you were fine. Ok, so it was never truly that simple, but you get my point. Now as internet surfers become more concerned about tracking and companies find new ways to follow you even more, things have gotten a bit crazy. Microsoft’s Edge wants to remember everything you do as does Chrome and Safari. This is presented as giving you a more complete and speedy internet experience, in reality it just creates a trove of data about you that can be used for good or bad.
- Details
- By Sean Kalinich
- Hits: 1533
More Articles …
Page 32 of 33