From The Blog
-
ConnectWise Slash and Grab Flaw Once Again Shows the Value of Input Validation We talk to Huntress About its Impact
Written by Sean KalinichAlthough the news of the infamous ConnectWise flaw which allowed for the creation of admin accounts is a bit cold, it still is one that…Written on Tuesday, 19 March 2024 12:44 in Security Talk Read 696 times Read more...
-
Social Manipulation as a Service – When the Bots on Twitter get their Check marks
Written by Sean KalinichWhen I started DecryptedTech it was to counter all the crap marketing I saw from component makers. I wanted to prove people with a clean…Written on Monday, 04 March 2024 16:17 in Editorials Read 1575 times Read more...
-
To Release or not to Release a PoC or OST That is the Question
Written by Sean KalinichThere is (and always has been) a debate about the ethics and impact of the release of Proof-of-Concept Exploit for an identified vulnerability and Open-Source…Written on Monday, 26 February 2024 13:05 in Security Talk Read 1109 times Read more...
-
There was an Important Lesson Learned in the LockBit Takedown and it was Not About Threat Groups
Written by Sean KalinichIn what could be called a fantastic move, global law enforcement agencies attacked and took down LockBit’s infrastructure. The day of the event was filled…Written on Thursday, 22 February 2024 12:20 in Security Talk Read 1080 times Read more...
-
NetSPI’s Offensive Security Offering Leverages Subject Matter Experts to Enhance Pen Testing
Written by Sean KalinichBlack Hat 2023 Las Vegas. The term offensive security has always been an interesting one for me. On the surface is brings to mind reaching…Written on Tuesday, 12 September 2023 17:05 in Security Talk Read 2131 times Read more...
-
Black Kite Looks to Offer a Better View of Risk in a Rapidly Changing Threat Landscape
Written by Sean KalinichBlack Hat 2023 – Las Vegas. Risk is an interesting subject and has many different meanings to many different people. For the most part Risk…Written on Tuesday, 12 September 2023 14:56 in Security Talk Read 1851 times Read more...
-
Microsoft Finally Reveals how they Believe a Consumer Signing Key was Stollen
Written by Sean KalinichIn May of 2023 a few sensitive accounts reported to Microsoft that their environments appeared to be compromised. Due to the nature of these accounts,…Written on Thursday, 07 September 2023 14:40 in Security Talk Read 2122 times Read more...
-
Mandiant Releases a Detailed Look at the Campaign Targeting Barracuda Email Security Gateways, I Take a Look at What this all Might Mean
Written by Sean KalinichThe recent attack that leveraged a 0-Day vulnerability to compromise a number of Barracuda Email Security Gateway appliances (physical and virtual, but not cloud) was…Written on Wednesday, 30 August 2023 16:09 in Security Talk Read 2097 times Read more...
-
Threat Groups Return to Targeting Developers in Recent Software Supply Chain Attacks
Written by Sean KalinichThere is a topic of conversation that really needs to be talked about in the open. It is the danger of developer systems (personal and…Written on Wednesday, 30 August 2023 13:29 in Security Talk Read 1890 times Read more...
Recent Comments
- Sean, this is a fantastic review of a beautiful game. I do agree with you… Written by Jacob 2023-05-19 14:17:50 Jedi Survivor – The Quick, Dirty, and Limited Spoilers Review
- Great post. Very interesting read but is the reality we are currently facing. Written by JP 2023-05-03 02:33:53 The Dangers of AI; I Think I Have Seen this Movie Before
- I was wondering if you have tested the microphone audio frequency for the Asus HS-1000W? Written by Maciej 2020-12-18 14:09:33 Asus HS-1000W wireless headset impresses us in the lab
- Thanks for review. I appreciate hearing from a real pro as opposed to the blogger… Written by Keith 2019-06-18 04:22:36 The Red Hydrogen One, Possibly One of the Most “misunderstood” Phones Out
- Have yet to see the real impact but in the consumer segment, ryzen series are… Written by sushant 2018-12-23 10:12:12 AMD’s 11-year journey to relevance gets an epic finish.
Most Read
- Microsoft Fail - Start Button Back in Windows 8.1 But No Start Menu Written on Thursday, 30 May 2013 15:33 in News Be the first to comment! Read 116522 times Read more...
- We take a look at the NETGEAR ProSafe WNDAP360 Dual-Band Wireless Access Point Written on Saturday, 07 April 2012 00:17 in Pro Storage and Networking Be the first to comment! Read 87468 times Read more...
- Synology DS1512+ Five-Bay NAS Performance Review Written on Tuesday, 12 June 2012 20:31 in Pro Storage and Networking Be the first to comment! Read 82026 times Read more...
- Gigabyte G1.Sniper M3 Design And Feature Review Written on Sunday, 19 August 2012 22:35 in Enthusiast Motherboards Be the first to comment! Read 80334 times Read more...
- The Asus P8Z77-M Pro Brings Exceptional Performance and Value to the Lab Written on Monday, 23 April 2012 13:02 in Consumer Motherboards Be the first to comment! Read 70986 times Read more...
Displaying items by tag: Hacking
Google's Jellybean To Be The Most Secure Version Of Android To-Date
 |
It looks like Google is finally stepping up to the plate when it comes to security in their Android Smartphone OS. For a number of years now opponents of Google’s desert themed mobile OS have complained Android does not have sufficient security. This makes it an unsuitable operating system. The fact that a large portion of these complaints come from the competition (Apple and Microsoft) meant that they were ignored by the large majority of people. It is also noteworthy that the openness of Android has allowed for mobile phone makers to highly individualize their Android offerings instead of relying on the stock version. Consumers have eaten this up and now you can see people defending their favorite version (HTC’s Sense UI over Samsung etc.) It is a great feature to the OS and one that has helped in in the market.
Researchers Find That Some ISP Supplied Wireless Routers May Have Almost No Security
 |
One of the biggest items we have talked about is the mentality of companies when it comes to protecting their customers. Sure, they will spend a little money to offer some rudimentary protection, but in the end if they can get away with not spending money to keep things safe, well they will. This pattern has been shown time and time again with multiple services online, at banks (think ATM hacks) and pretty much anywhere there is a way to talk to the computer systems in question. Now, a pair of researchers has found that Time Warner, Comcast, Cox and probably many more are barely providing security for their customers who use their recommended hardware.
Apple's In-App Purchase System Bypassed with Simple Tools; Is This The Next Attack Vector?
 |
As we have told all of you before no system is secure. We have watched now as Android malware writers are using social engineering to mass-market spam and now we are seeing the first proof of concept of a method to “hack” Apple’s In-App purchase feature. We mentioned in our recent coverage of the Anrdoid.Dialup malware that this feature was not only vulnerable, but also could be used as a vector for attack and the installation of other malware.
nVidia Developer Zone and Android Forums Get Added To The List of Attacked Sites with Possible Data Theft
 |
We have two additional hacks to report this morning. The first was a little shocking as it has been learned that nVidia’s Developer Zone form was under attack. Although details of this attack are small it does appear that nVidia recognized that there was an attack on the forum and shut it down to prevent additional attack. However nVidia warns that the hashed passwords for the forum may have been accessed. Right now the forum is still down with only a canned message in its place warning users about the attack and advising them to change their passwords especially any passwords that might be identical across multiple sites.
Yahoo Is The Latest In A String Of Breaches That Have Yielded User Passwords Showing Serious Flaws in IT Security...
 |
We have said this once and we will say it again; 2012 will be remembered as the year of the breach. This year alone we have seen a significant number of services penetrated with relative ease and user account information pulled out at an alarming rate. So far this year we have watched as Linkedin, eHarmony, Last.fm, Formspring, League of Legends and more have been compromised and literally Millions of user account details have been posted to the Internet. It is a very disturbing trend considering the rather big push to the cloud for so many critical services (like hosting our personal records).
Anonymous Launches OpPedoChat To Wipe Child Abuse Sites From The Internet
 |
Anonymous is back in the headlines; this time it is not for doxing a large and corrupt corporation or a DDoS attack on a government website. This time it is all about the kids. In what certain members of the collective are calling OpPedoChat the activist movement it targeting websites and forums that cater to pedophiles. The group has vowed to wipe them from the internet and expose anyone that uses these sites.
Military Drone Hacked By Spoofing GPS; We Are Not Surprised
 Although the media world seems shocked by the news that the unmanned drones in use by the military are vulnerable to cyber-attacks we wonder exactly why. I mean come on how many security breaches of high-level “secured” sites have to happen before someone gets it? There really is no such thing as a secure system. This has been shown time and again going back to the first encryption methods. If you have some access to the system you can get in.
Although the media world seems shocked by the news that the unmanned drones in use by the military are vulnerable to cyber-attacks we wonder exactly why. I mean come on how many security breaches of high-level “secured” sites have to happen before someone gets it? There really is no such thing as a secure system. This has been shown time and again going back to the first encryption methods. If you have some access to the system you can get in.
New Tool Called Daedalus Developed By Japan's NICT For Monitoring The "Darknet"
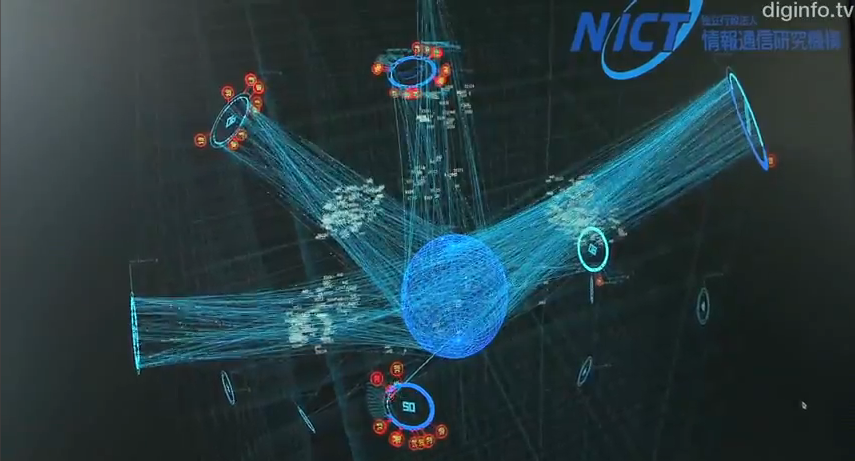 There is an interesting habit in the world of science; when you cannot explain or categorize something add “dark” to the front of the regular word and that makes it all ok. We have seen this in astrophysics, particle physics, theoretical physics, and now to IT. With this maxim we get Dark Matter, Dark Energy and my favorite “Darknet” It just sounds cool right?
There is an interesting habit in the world of science; when you cannot explain or categorize something add “dark” to the front of the regular word and that makes it all ok. We have seen this in astrophysics, particle physics, theoretical physics, and now to IT. With this maxim we get Dark Matter, Dark Energy and my favorite “Darknet” It just sounds cool right?
Fujitsu R&D Breaks a Cryptography World Record As It Cracks a 923-Bit Cypher
I am not even sure how many times I have said this, but here it is again; what man can lock (encrypt etc) man can unlock. This has been proven again as Fujitsu has announced a world record breaking event in crypto cracking. The electronics company’s research and development arm has successfully cracked and cypher that was 278 digits long (this equates to 923 bit). The feat surpasses a breakthrough in 2009 by 74 digits.
am not even sure how many times I have said this, but here it is again; what man can lock (encrypt etc) man can unlock. This has been proven again as Fujitsu has announced a world record breaking event in crypto cracking. The electronics company’s research and development arm has successfully cracked and cypher that was 278 digits long (this equates to 923 bit). The feat surpasses a breakthrough in 2009 by 74 digits.
Reckz0r Returns After a Week Off With a Hack of 79 Banks
 About five days ago a hacker that goes by the name of Reckz0r kicked off a new group called SpexSec which created quite a stir. We talked about the group’s appearance and just as sudden disappearance. They showed up made three dumps of data and after a short exchange with someone on Twitter all three of the SpexSec members announced their retirements.
About five days ago a hacker that goes by the name of Reckz0r kicked off a new group called SpexSec which created quite a stir. We talked about the group’s appearance and just as sudden disappearance. They showed up made three dumps of data and after a short exchange with someone on Twitter all three of the SpexSec members announced their retirements.
